ttps://www.hackthebox.com/achievement/machine/35564/444
If you wanna try the box without walk through just follow the bold text.Summary
Hi all, this time we are looking into the RouterSpace box. The box starts with revealing it’s ports 80 and 22. On visiting the web page running on port 80 its found that its a static page with a Download button which downloads and android application. Instantly after installing the application, we get a Check Status button. The button checks if the internet is working or something by pinging 0.0.0.0, from routerspace.htb server which can be identified from monitoring the traffic. On further enumeration it is identified that the parameter is passed as JSON and the value of the IP is vulnerable to command injection. The vulnerability can be used to add ssh key to authorized_keys and get a ssh session. LinPEAS reveals that version of sudo is vulnerable and exploit is available like a wrapped present. The exploit is delivered to the box and executed to get a root shell.
Actual Walk through
As we all would start a box, identification of services and ports is the initial step and thy shall be.
Scanning and Enumeration
Started with classic nmap scan with -sCV flag almost instantly identifying ports 22 and 80.

nmap result showing ports 80 and 22
Ssh port seems like the classis control port for HBT boxes so the focus shifts to port 80.
Opening the IP in a web browser shows a standard colorlib site with some content that makes sense rather than the usual “Lorem Ipsum” page.

Web service on port 80
On looking around, some artefacts are found like a domain name in one of the images.

Still don’t know if it was intended to be shown here.
The found domain name is immediately added to the /etc/hosts file (just in case). Also the domain name is checked in browser to see if any V-host routed sites are available (nop..).

Added domain name to hos file
It is also identified that a download button is on the home page which downloads an APK file.

The download button.
The APK file is instantly installed in Genymotion(my preferred choice of android poison).

Successfully installed.
Before any shenanigans, the application is opened to check what it does.

Only one page that checks the router.
The application doesn’t do much other than displaying “Hey ! Router is working fine!” when pressed the only button on the application.
So it hacking time and we fire up burp and setup proxy to see the traffic.
These are the proxy settings if this is new to the reader:
On Mobile
- Click and hold on the wireless icon on android.

- Click and hold on the WiFi name

Select modify network
- Select Manual in the proxy settings.
- Type in the IP of the Virtual interface created for Genymotion(
ifconfig). - Port being any non common one preferably (8081 this time).

In Burp
- Select the Proxy tab > Options.
- In the Proxy Listener settings > Add

- Select the IP given in Mobile (Virtual interface of genymotion)
- Port the same given in mobile.

Exploitation
After setting up the proxy, use the application and monitor the application traffic.

Request to routerspace.htb
Instantly Input validation and injection attacks were the first candidates. Listing some of them below.
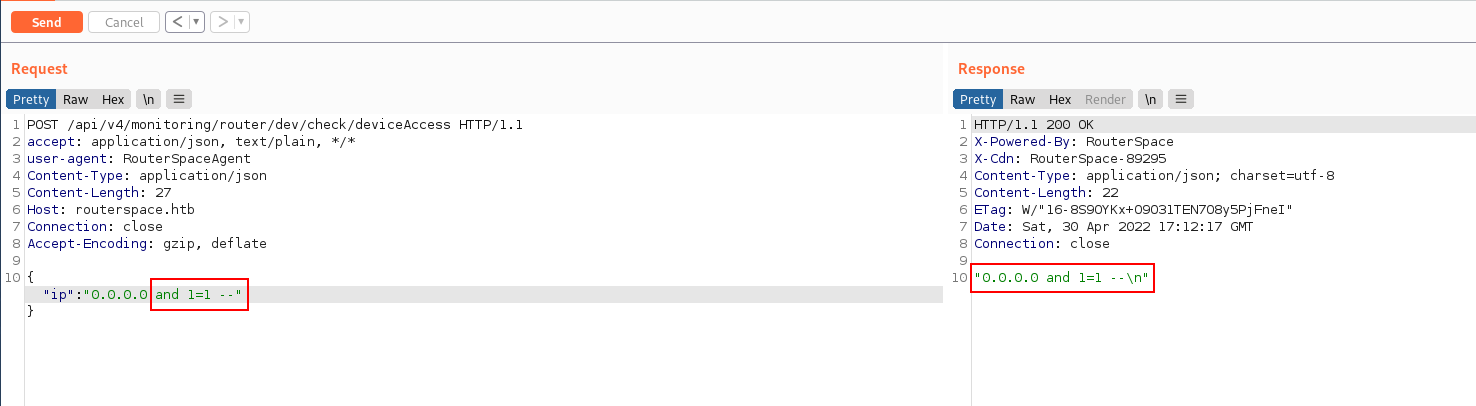
SQLi

SSTI

Directory Traversal
Command injection was successful with pipe as command separator works (This might be the first try of people who have seen DVWA)

Command injection works.
Next step for anyone who gets a command injection is to gain an interactive session.
My preferred method is to gain ssh session so, started checking the authorized_keys

List /home dir

listing home dir of user

checking user flag in between
checking all the files in paul’s home directory.

This looked weird.
Checking with ls -a

this looks nice and .ssh is available
check if authorized_keys is available or id_rsa private key is available

authorized_keys found
Generate a ssh key pair.

Generated ssh key pair
Here is the created ssh key.

Next we have to use the RCE or remote code execution to inject the ssh key to the authorized_keys file in the victim machine.
For this I am using the echo command.

Added ssh key to the authorized_keys file
Now that we have our key in the victims authorized_keys file we can directly take ssh to the machine using our keypair
ssh -i key paul@routerspace.htb

successfully got a ssh session
Privilege Escalation
In order to escalate our privilege from the Paul user to root we have to do some enumeration. My choice of poison for now is linpeas (cuz this is a linux box).
I transferred the script to the machine with scp
scp -i key linpeas.sh paul@routerspace:/tmp/linpeas.sh

Linpeas moved from my attacker machine to the victims tmp folder
Running Linpeas showed some interesting results
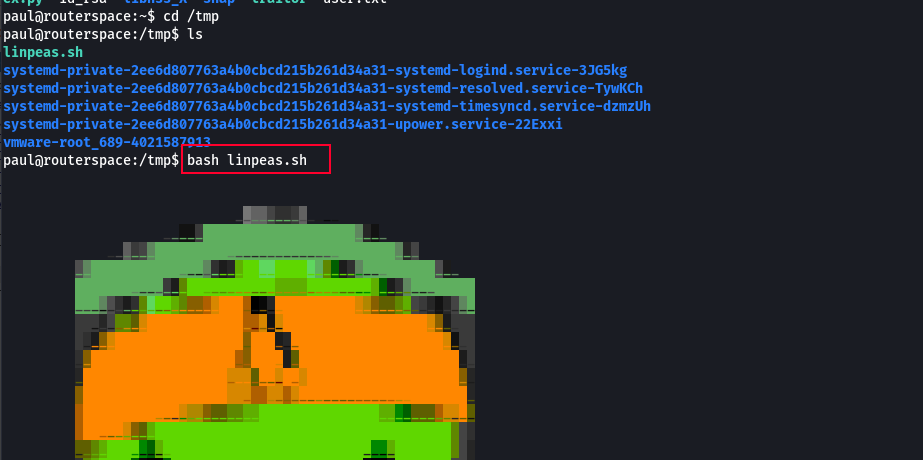
Running linpeas
It is seen that the sudo version running on the box is a vulnerable version.

Linpeas identified sudo version
On quick google search it is seen that the version is vulnerable to a Privilege Escalation Vulnerability.

Sudo version vulnerable to CVE-2021-3156

Found the exploit code for the vulnerability.
Cloned the repo and I was ready to run the exploit.
However when I compiled the code and executed on the machine I was not able to elevate my privilege. After banging my head against my desk I decided to move the exploit on to the victim machine and compile there and then exploit it. So I moved the exploit code to the victim machine.

moved the files one by one
Compiled the exploit in the tmp directory.

compiled the exploit code
On execution of the exploit I got a root shell ! and Viola… I have done it again.

And I am root !